The 2018 was the year of the CPU related threats, starting with the Meltdown and Spectre bugs affecting several processors, but with most of issues related to Intel based CPU.
Unfortunately, this was only the beginning and many other bugs were discovered later. And we’re probably just at the tip of the iceberg.
New Meltdown and Spectre variants have been discovered, as also other type of bugs, like, for example, L1 Terminal Fault aka Foreshadow.
The main problem, is that those bugs are, in most case, difficult to fix, and may have several performance impact. Also, redesign a CPU architecture is not so easy and take (a lot of) time… most of the CPU that we are using today have been designed some years ago…
Now there are again new type of speculative execution issues, with the Microarchitectural Data Sampling (MDS) vulnerabilities, a set of weaknesses in Intel x86 microprocessors that leak data across protection boundaries that are architecturally supposed to be secure.
Actually seems a bug affecting (still) only Intel’s CPUs with a very huge list of affected processors. Instead, AMD just says:
Based on our analysis and discussions with the researchers, we believe our products are not susceptible to ‘Fallout’, ‘RIDL’ or ‘ZombieLoad Attack’ because of the hardware protection checks in our architecture.
On affected Intel CPU, there is the possibility of reading data buffers found between different parts of the processor and there are these possible attacks:
- Fallout (CVE-2018-12126) — a leak of data being stored from store buffers
- RIDL (CVE-2018-12127, CVE-2018-12130 and CVE-2019-11091) — a leak from various internal processor buffers of data being loaded and stored
- ZombieLoad (CVE-2018-12130) — a leak of already-loaded data from a processor’s fill buffer
As usually the fixes are not only at hardware level (microcode update), but usually at operating systems, virtualization level, applications (like web browsers), …
For the microcode, Intel fixes in its processors starting shortly before the public announcement of the vulnerabilities. But all the hardware vendors need to include the update in their BIOS and firmware. For example, for Dell EMC PowerEdge server, see this link: Dell EMC Server Security Notice for Intel-SA-00233.
For the operating systems, on 14 May 2019, a mitigation was released for the Linux kernel, and Apple, Google, Microsoft, and Amazon released emergency patches for their products to mitigate ZombieLoad.
For the different hypervisors, each vendor has to release the proper function to support the remediation at this level.
For example, VMware has realize this Security Advisories:
- 2019-05-14 – Microarchitectural Data Sampling (MDS) – VMSA-2019-0008
The solution from VMware is very similar to the one for L1 Terminal Fault (L1TF), with a new ESXi Side-Channel-Aware (SCA) Scheduler. Note that also vSphere 5.5 is still supported.
Note that there are two different versions of the ESXi SCA scheduler and recent versions of ESXi have the new SCA v2:
- ESXi 6.7u2 (13006603) and future release lines of ESXi include the ESXi Side-Channel-Aware Scheduler v2
- Prior release lines such as 6.5, 6.0, and 5.5 cannot accommodate this new scheduler.
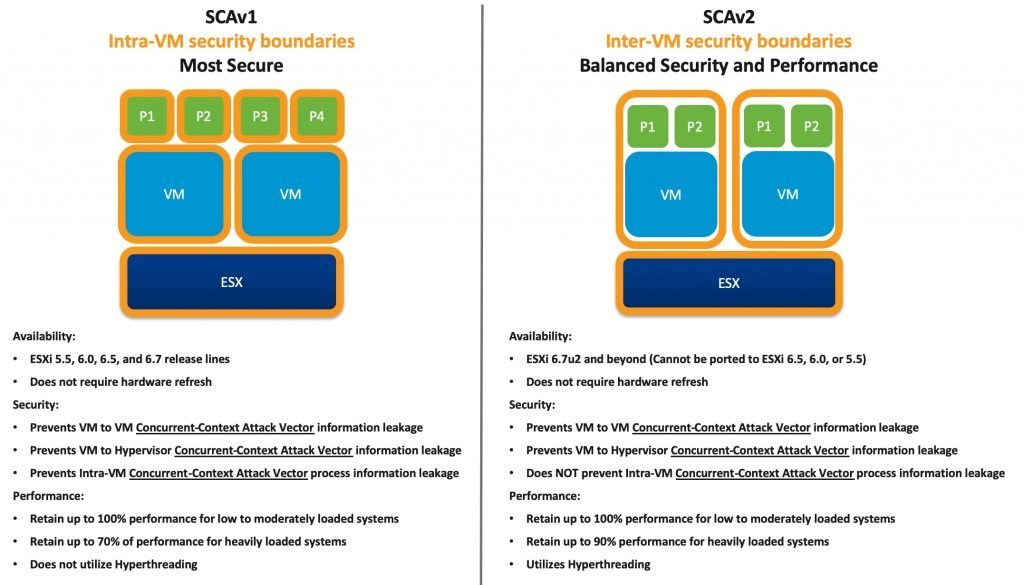
VMware has published a white paper entitled Performance of vSphere 6.7 Scheduling Options which provides a more detailed look into the performance differences between SCAv1 and SCAv2.
For more information see also:
- The SPECTRE story continues … now it is MDS – With also a great paper on performace impact analysis
- Which vSphere CPU Scheduler to Choose
- VMware KB 67577 – Implementing Hypervisor-Specific Mitigations for Microarchitectural Data Sampling (MDS) Vulnerabilities (CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, and CVE-2019-11091) in vSphere (67577)



