Reading Time: < 1 minuteRecently VMware has released a few security patches that will prevent a guest from execute code on the ESXi host and breaking the isolation of a virtual machine.
This has been possible based on heap buffer overflow and uninitialized stack memory usage in SVGA, using this bug may allow a guest to execute code on the host.
Note that this particular issue impacts ESXi 6.0 or later as also latest version of VMware Workstation, Player and Fusion.
Available VMware KB articles for these issues are:
Here the complete status of the affected versions:
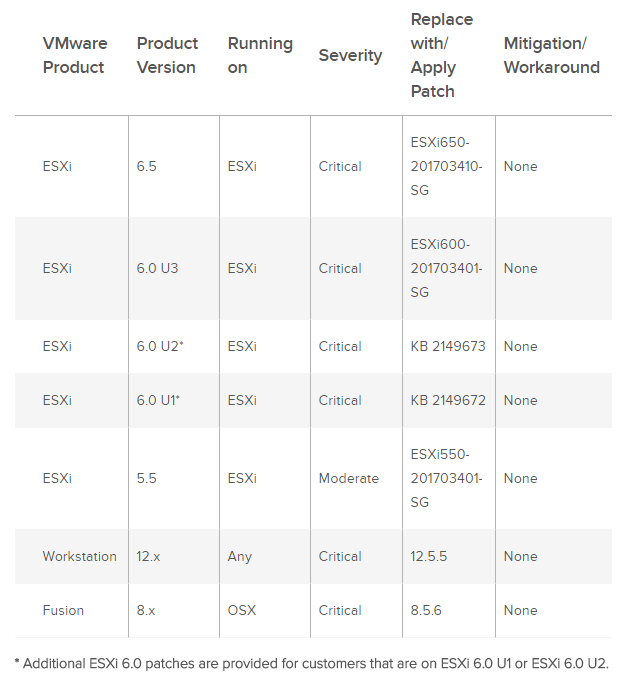
For more informations see the VMware Security Advisories VMSA-2017-0006.
Related Posts
VMware ESXi 5.0 Patch ESXi500-201111401-BGVMware ha da poco rilasciato una patch per ESXi™ 5.0, che risolve il seguente problema: The software iSCSI slow boot issue resolved (descritto in VMware KB 2007108) Per maggiori informazioni vedere le note di rilascio della patch per ESXi 5.0.A new VMware® ESXi™ 5.0 Patch…
vSphere 5 downloadFinally the vSphere 5 download is now available on VMware site: http://downloads.vmware.com/d/info/datacenter_cloud_infrastructure/vmware_vsphere/5_0 VMware ESXi 5.0 (Build 469512) VMware vCenter 5.0 (Build 456005) Also the official documents is now available: http://www.vmware.com/support/pubs/vsphere-esxi-vcenter-server-pubs.html
-
VMware acquires E8 SecurityVMware has acquired the technology and team of E8 Security. With this acquisition, VMware is further reinforcing its commitment to deliver the industry’s first intelligence-driven digital workspace to empower the employee experience and drive predictive security. Adding E8 Security’s capabilities to VMware's digital workspace platform,…
Virtualization, Cloud and Storage Architect. Tech Field delegate.
VMUG IT Co-Founder and board member. VMware VMTN Moderator and vExpert 2010-24. Dell TechCenter Rockstar 2014-15. Microsoft MVP 2014-16. Veeam Vanguard 2015-23. Nutanix NTC 2014-20.
Several certifications including: VCDX-DCV, VCP-DCV/DT/Cloud, VCAP-DCA/DCD/CIA/CID/DTA/DTD, MCSA, MCSE, MCITP, CCA, NPP.



