Veeam Backup & Replication 12 supports different malware detection methods that works in different way and can be used together to reach different scopes. Note: new features have been added in version 12.3!
The first main diffecence is that some works inline (during the backup process on the source data) and other works with a post-processing directly on restore points saved on the repositories.
For this reason also the load of those malware detection activities can be on different Veeam components, basically on the proxy servers for inline methods and the mount servers for the post-processing methods.

This table summirizes the different malware detection methods available on Veeam Backup & Replication 12.x (for more information see: https://helpcenter.veeam.com/docs/backup/vsphere/malware_detection_methods.html?ver=120):
| Malware detection feature | Detection method | Type of objects analyzed | Objects marked as… | Notes |
|---|---|---|---|---|
| Guest Indexing Data Scan | Inline file system activity analysis | Guest OS indexing data | Suspicious | During the backup job, detects the following malware activity:Known suspicious files and extensions, Renamed files, Deleted files |
| Inline Scan | Inline entropy analysis | Blocks in a data stream | Suspicious | During the backup job, detects the following malware activity: Encrypted files, Onion links or Ransom notes |
| Scan Backup and Secure Restore | Rule-based detection (YARA) | Restore points | Infected | During the Scan Backup session, does one of the following:Finds the last clean restore pointAnalyzes the content for specific informationDuring the restore session with the Secure Restore option, detects malware activity as specified in the YARA rule. |
| Secure Restore and Scan Backup | Antivirus scan | Restore points | Infected | During the Scan Backup session, finds the last clean restore point.During the restore session with the Secure Restore option, detects malware activity as specified in the antivirus configuration file |
| Veeam Incident API | Third-party malware protection solution | Depends on the configuration of the malware protection solution | Infected | Uses Veeam Incident API to send a request about detected malware activity to Veeam Backup & Replication. For more information, see Veeam Backup & Replication REST API Reference |
Each of them has diffent settings, different limitations, different requirements, different way to investigate on the results.
For a general approach see this interesting blog post: https://community.veeam.com/blogs-and-podcasts-57/veeam-malware-detection-a-forensics-analysis-how-to-guide-7829
Guest Indexing Data Scan
To scan guest indexing data, Veeam Backup & Replication uses file system activity analysis. During the backup job, the following malware activity can be detected:
- Known suspicious files and extensions specified in the SuspiciousFiles.xml file
The file is located on the backup server in the Veeam Backup & Replication product folder
The default path is: C:\Program Files\Veeam\Backup and Replication\Backup\SuspiciousFiles.xml- Managing List of Suspicious Files and Extensions
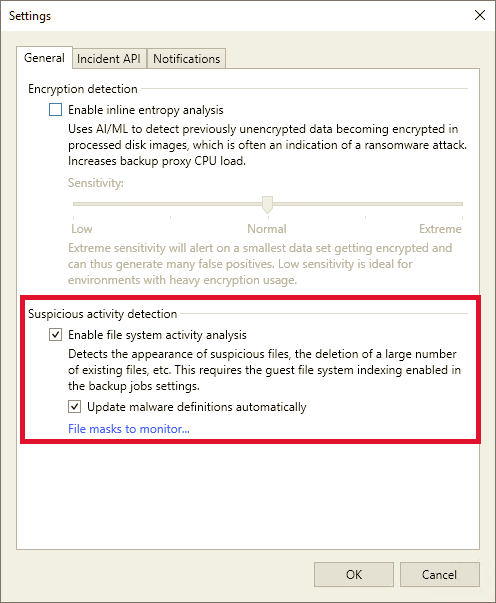
To keep the list of suspicious files and extensions up-to-date, select the Update malware definitions automatically check box
If the option is enabled, Veeam Backup & Replication will communicate with the Veeam Update Server (vbr.butler.veeam.com) daily at 12:00 AM and download the latest version of the SuspiciousFiles.xml file – note that the usage of a proxy is not yet supported (because there is no way to configure it)
To manually download and update the file, follow https://www.veeam.com/kb4514 - Do not edit the SuspiciousFiles.xml directly – If you want to customize the list of suspicious files and extensions, you can do it in the malware detection settings. For more information, see Managing List of Suspicious Files and Extensions.
- Managing List of Suspicious Files and Extensions
- Multiple files renamed by malware. A malware detection event will be created if the following conditions are met:
- There must be at least 200 renamed files with the same or different extensions.
- These extensions are not specified in the SuspiciousFiles.xml file.
- Multiple files deleted by malware. A malware detection event will be created if at least 25 files with specific extensions or 50% of files with specific extensions are deleted.
Note that this functionality is enabled by default when you install or upgrade to Veeam Backup & Replication 12.1 (build 12.1.0.2131).
You can only scan guest indexing data when backing up the following machines:
- VMware VMs including VMware Cloud Director VMs (with guest processing enabled in the backup job)
- Hyper-V VMs (with guest processing enabled in the backup job)
- Machines with Veeam Agent for Microsoft Windows operating in the managed by backup server mode (image-level and volume-level backup)
Note that detection of “sleeping” malware is not supported by this method.
Information about detected malware activity is stored in malware detection logs. The path by default: C:\ProgramData\Veeam\Backup\Malware_Detection_Logs.
Starting from Veeam Backup & Replication 12.1.1 (build 12.1.1.56), you can also view the detailed log in the Event Details window. For more details, see Viewing Malware Detection Events.
To enable the guest indexing data scan, do the following:
- From the main menu, select Malware Detection > General.
- In the Suspicious activity detection field, select the Enable file system activity analysis check box.
- Make sure that you enable guest file system indexing for the necessary backup job. For more information, see Specify Guest Processing Settings.
Inline Scan
To scan blocks in a data stream, Veeam Backup & Replication uses inline entropy analysis. During the backup job, the following malware activity can be detected:
- Files encrypted by malware. A malware detection event will be created if the amount of encrypted data exceeds scan sensitivity limits.
See KB 4632 (How to Investigate ‘Encrypted Data Event’ from Malware Detection). - Text artifacts created by malware:
- V3 onion addresses that consist of 56 symbols in the [a-z2-7]{56}.onion format. For example, vykenniek4sagugiayj3z32rpyrinoadduprjtdy4wharue6cz7zudid.onion.
- Ransomware notes created by Medusa and Clop
Note that for text artifacts, actually no details are provided on which files are considered Suspicious… but you can use guest OS investigation tools or scan with specific YARA rules
A malware detection event will be created if a new restore point contains more onion addresses or ransomware notes than the previous restore point selected for comparison. If both restore points contain the same number of onion addresses or ransomware notes, a malware detection event will not be created. For more details, see How Inline Scan Works.
All Inline Entropy Scan events are noted in a single log file located at: C:\ProgramData\Veeam\Backup\Svc.VeeamDataAnalyzer.log .
| NOTE |
| Inline scan is disabled by default when you install or upgrade to Veeam Backup & Replication 12.1 (build 12.1.0.2131) If you want to use this functionality, be aware that it may increase CPU usage (10-15% on average) on the backup proxy or Veeam agent, depending on the workload type and amount of data Also remember that the Veeam Catalog space usage will increase with malware detection enabled |
You can scan blocks in a data stream when backing up the following machines:
- VMware VMs including VMware Cloud Director VMs
- Hyper-V VMs
- Machines with Veeam Agent for Microsoft Windows operating in the managed by backup server mode (volume-level backup only)
Note that the inline scan has the following requirements and limitations:
- Scanning is supported only for simple volumes and for the following file systems: NTFS, ext4, ext3, ext2. Note that xfs is not yet listed.
- Scanning dynamic disks and disks encrypted by BitLocker is not supported.
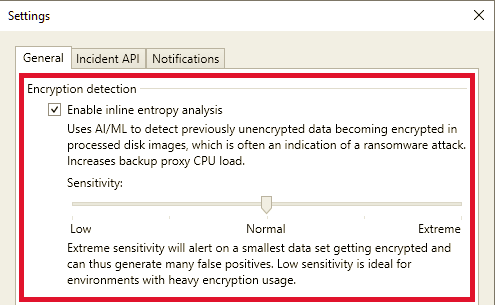
To enable inline scan, do the following:
- From the main menu, select Malware Detection > General.
- In the Encryption detection field, select the Enable inline entropy analysis check box.
- Specify the scan sensitivity depending on your backup data and backup infrastructure capabilities. The default value is Normal.
For more information see also: https://community.veeam.com/blogs-and-podcasts-57/deep-dive-inline-malware-detection-6362
Secure Restore
Secure restore allows you to scan restore points with antivirus software before restoring the machine to the production environment. Starting from Veeam Backup & Replication 12.1 (build 12.1.0.2131), you can also scan restore points with YARA rules.
Secure restore is available for the following operations:
- Instant Recovery
- Instant Disk Recovery
- Virtual Disks Restore
- Entire VM Restore
- Restore to Microsoft Azure
- Restore to Amazon EC2
- Restore to Google Compute Engine
- Disk Export
Veeam mounts the restore Point to a Mount Server (that can be only Windows at this time) under C:\VeeamFLR\<machinename> and uses the Antivirus and/or the YARA rules on the Mount Server to scan the content of the disks in the restore point.
Consider the following:
- You can perform secure restore only for Microsoft Windows machines.
- Secure restore for Linux machines is not yet implemented, but there are some interesting scripts that add this capability… for example see Secure Restore for Linux VM
- Veeam Backup & Replication does not perform malware scan for disks or volumes that cannot be mounted to the mount server. For example, Storage Spaces disks or ReFS volumes (if ReFS is not supported by the mount server OS) are skipped from the scan and restored in a regular way.
- You need a Veeam Data Platform Advanced license in order to use YARA rules (you don’t need to deploy VeeamONE).
Scan Backup
Scan Backup is a new feature of Veeam Backup & Replication 12.0 that allows to scan restore points with antivirus software without restoring the machine. Starting from Veeam Backup & Replication 12.1 (build 12.1.0.2131), you can also scan restore points with YARA rules.
You can run the Scan Backup session to perform the following operations:
- Find the last clean restore point after a recent malware attack.
- Find the last clean restore point if the date of the malware attack is unknown.
- Find some specific information, for example, sensitive data.
Veeam mounts the restore Point to a Mount Server (that can be only Windows at this time) under C:\VeeamFLR\<machinename> and uses the Antivirus and/or the YARA rules on the Mount Server to scan the content of the disks in the restore point.
You can run the Scan Backup session for the following backups:
- Image-level virtual machine backups and backup copies only of Microsoft Windows VMs (VMware, Hyper-V, Cloud Director, Nutanix AHV, OLVM and RHV)
- Physical machine backups and backup copies (Microsoft Windows only)
The following entities are not supported:
- Image-level virtual machine backups and backup copies of Linux VMs. Anyware there are some un-official scripts that implement this feature… for example see VBR Backup Scan – Updates
- Backups stored in the Veeam Cloud Connect repository.
- Backups stored in the archive tier of the scale-out backup repository.
- Storage snapshots
Note that you need a Veeam Data Platform Advanced license in order to use YARA rules (you don’t need to deploy VeeamONE).











