The new VMware Virtual SAN (or vSAN) 6.6 adds several enchaments and new features as described in the announce notes.
Some interesting news are related to security aspects and how data-at-rest could be protected: one option could be new vSphere 6.5 VM encryption format but now it’s also possible use the native vSAN encryption. Duncan’s post explains the difference of those two approaches.
VM encryption has some performance impacts, it require Enterprise Plus editions and works on top (using VAIO), so encrypted blocks do not dedupe (or compress) well at vSAN level.
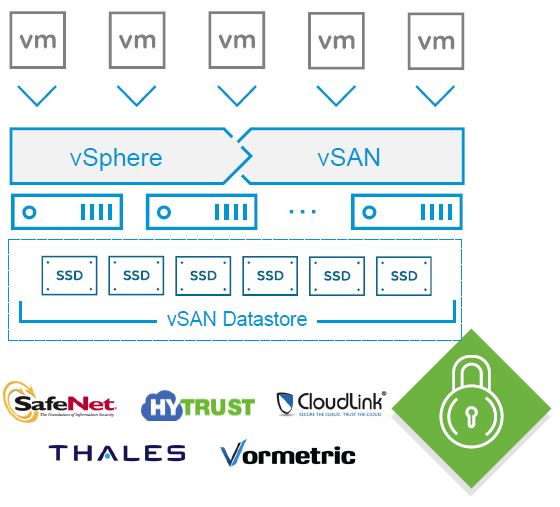
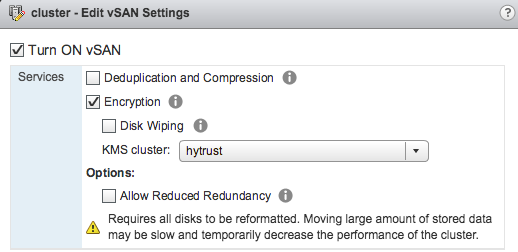
The new vSAN feature (that require vSAN Enterprise) it’s enabled at cluster level for the entire vSAN datastore and all objects in it and can support hybrid, all-flash and stetched clusters configuration:
It really easy to be configured and support all vSAN features. During the activation of this feature it’s also possible wipe all disks to be sure that all data are removed (but there is no
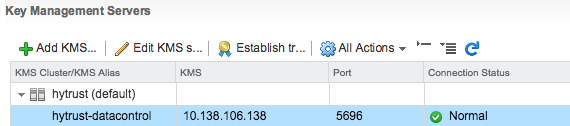
Also it could be integrated with all KMIP compliant key management technologies (included SafeNet, Thales, Vormetric, CloudLink, Hytrust, …) and does not require specific SED (Self Encrypting Drive) at hardware level, making it a clear and complete software solutions.
For data-in-move or data in transit actually it’s possible use VM encryption to encrypt vMotion traffic, but all other traffic could be clear (or need to be proctect with SSL connections). For vSAN backend, note that data travels unencrypted, but it is written encrypted to the cache layer, so you need to keep the vSAN traffic protected and isolated.
See also: vSAN 6.6 Encryption Configuration.