Spectre and Meltdown bugs are something from the past (my last blog post was about some Meltdown and Spectre variants) or not? Of course that’s not true… we have only start to stratch the attack surface of CPU.
Now there are additional chapters of Spectre saga.
Unfortunately, researchers at ETH Zurich have discovered another bug that affects a number of Intel processors, dating back to the 2018 Skylake architecture.
There are multiple CVE as listed in the Intel page. The most important are CVE-2025-20623 (related to iCore CPU) and CVE-2024-45332 (related to Xeon CPU).
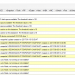
| Product family | Vertical Segment | CVE ID | CPU ID | Platform ID |
| 12th Generation Intel® Core™ Processor Family Intel® Pentium® Gold Processor Family Intel® Celeron® Processor Family | Desktop Mobile Embedded | CVE-2024-45332 | 906A4 906A3 90675 90672 B06E0 | 0x80 0x07 0x110x40 |
| 2nd Generation Intel® Xeon® Scalable Processors | Server Workstation | CVE-2024-45332 | 50657 50656 | 0xBF |
| 9th Generation Intel® Core™ Processor Family Intel® Xeon® E Processors | Mobile Desktop Embedded Server | CVE-2024-45332 | 906ED | 0x22 |
| 10th Generation Intel® Core™ Processor Family Intel® Xeon® E Processor | Desktop Mobile Embedded Server | CVE-2024-45332 | A0652 A0655 A0653 A0660 806EC A0661 | 0x22 0x20 0x80 0x94 |
| 3rd Generation Intel® Xeon® Scalable Processor Family | Server | CVE-2024-45332 | 5065B | 0xBF |
| 10th Generation Intel® Core™ Processor Family | Mobile | CVE-2024-45332 CVE-2025-20623 | 706E5 | 0x80 |
| 3rd Generation Intel® Xeon® Scalable Processor Family | Server Embedded | CVE-2024-45332 | 606A6 606C1 | 0x87 0x10 |
| Intel® Core™ Ultra Family | Mobile Desktop | CVE-2024-45332 | A06A4 | 0x7 |
| 13th Generation Intel® Core™ Processor Family 14th Generation Intel® Core™ Processor Family Intel® Pentium® Gold Processor Family Intel® Celeron® Processor Family 13th Generation Intel® Core™ i7 processors | Mobile Desktop | CVE-2024-45332 | B06A2 B06A3 B0671 B06F2 B06F5 | 0xe0 0x32 0x07 |
| Intel® Xeon® E processor family | Server | CVE-2024-45332 | B0671 | 0x1 |
| Intel Pentium® Processor G7400/G7400T | Server | CVE-2024-45332 | 90675 | 07 |
| 11th Gen Intel Core Intel® Core® i7-11700T Processor Intel® Core® i7-11700 Processor Intel® Core® i5-11400T Processor Intel® Core® i5-11400 Processor Intel® Core® i5-11500T Processor Intel® Core® i5-11500 Processor Intel® Xeon® E Processor | Desktop Embedded Server | CVE-2024-45332 | A0671 | 0x02 |
| 4th Generation Intel® Xeon® Scalable processors | Server Workstation | CVE-2024-45332 | 806F7 806F8 | 0x87 0x10 |
| 5th Generation Intel® Xeon® Scalable processors | Server Workstation | CVE-2024-45332 | C06F2 | 0x87 |
| 11th Generation Intel® Core Processor Family | Mobile Embedded | CVE-2024-45332 | 806C1 806C2 806D1 | 0x80 0xC2 |
| 8th Generation Intel® Core™ Processors | Mobile Embedded | CVE-2024-45332 | 806EC | 0x94 |
| Intel® Pentium® Processor Silver Series Intel® Celeron® Processor J Series Intel® Celeron® Processor N Series | Desktop Mobile | CVE-2024-43420 | 706A8 | 0x01 |
| Intel® Core™ Ultra 5, 7, 9 | MobileDesktop | CVE-2024-45332 | B0650C0652C0662C0664 | 01 |
| Intel® Core™ Ultra 5, 7, 9 | Mobile Embedded | CVE-2024-45332 | B06E0 | 01 |
| Intel® Xeon® 6 processor family | Server | CVE-2024-45332 | A06F2 | 01 |
| Intel® Atom® Processors P6000 | Networking Server | CVE-2024-45332 | B0664 | 01 |
Intel recommends that users of affected Intel® Processors update to the latest version provided by the system manufacturer that addresses these issues.
On May 1, Intel issued yet another microcode update for the Raptor Lake and Raptor Lake Refresh processors. Those processors could degrade over time due to elevated operating voltages, Intel said last July. But the recent update was designed to prevent instability on systems “running multiple days with low-activity and lightly-threaded workloads” — or machines that weren’t working at their full capacity.
The performance impact of the microcode patch will depend by the CPU family: 8,3% of performance degradation for famly Rocket Lake (11 generation), 2,7% for Alder Lake and 1,6% for Skylake.
We will see if there will be also some patches for OSes and hypervisors or the microcode update will be enough.