Meltdown and Spectre are critical vulnerabilities existing in several modern CPU: these hardware bugs allow programs to steal data which is currently processed on the computer. Meltdown and Spectre can affect personal computers, mobile devices, server and several cloud services.
There isn’t a single simple way to minimize those security risks, because you need to patch different levels of your stack. For a VMware environment, there are some tools to check your status (and also to help you to apply the right patches).
One interesting tool is Runecast Analyzer that, starting with version 1.6.6 (now there is v1.6.8) it can help with Meltdown and Spectre patching detection and requirements, also in the trial mode (that it’s limited to 14 days from the installation).
The nice aspect is that Runecast Analyzer works on a virtual appliance that can be deployed and become up and running in few minutes. Also, the overall setup is super fast, including a short time for the download (the virtual appliance file is little more than 1 GB), so perfect to run check your environment. And the health check is not limited to those issues, but according to all VMware KB (but note that some other checks are not available in the trial version.
The Runecast Analyzer appliance is distributed in the OVA form, as a single file, that can be deployed on the existing vSphere infrastructure that you want to check. You can deploy also with the new vSphere (HTML5) Client without any issues (some OVF deployment does not work with this client).
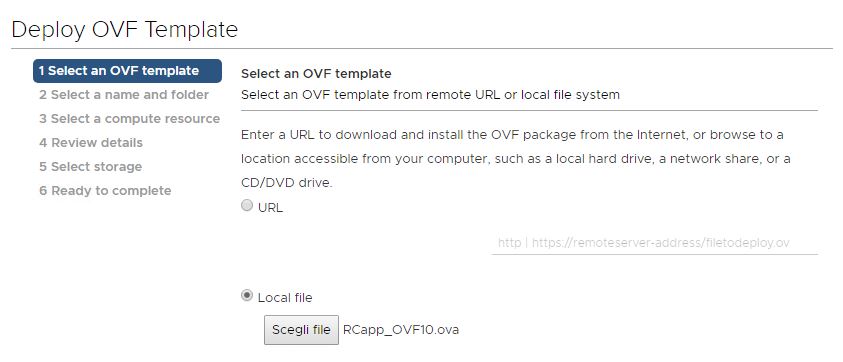
Select your OVA file (RCapp_OVF10.ova is the file name):
Then choose a VM name, a VM folder location and the right compute resources location (cluster or resource pool). At this point you will have a small summary: 
Now you can agree with the license file and choose the virtual appliance sizing: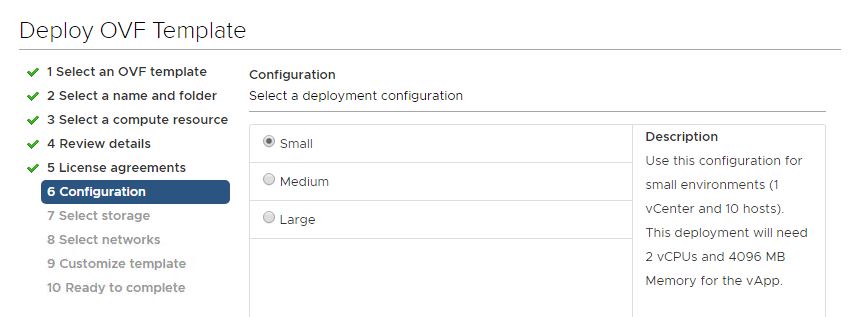
The deployment process has three different size (small/medium/large) with the following minimum of resources:
- Small (use this configuration for small environments: 1 vCenter and 10 hosts)
▪ 2 vCPU
▪ 4 GB RAM
▪ 90GB Storage
▪ 100Mbit network (1GBit or above recommended) - Medium (use this configuration for medium deployments: 5 vCenters and 100 hosts)
▪ 4 vCPU
▪ 8 GB RAM
▪ 90GB Storage
▪ 100Mbit network (1GBit or above recommended) - Large (use this configuration for large deployments: up to 15 vCenters and 250 hosts )
▪ 8 vCPU
▪ 32 GB RAM
▪ 90GB Storage
▪ 100Mbit network (1GBit or above recommended)
Now you can choose the storage location (and the disk provisioning, in thick provisioning the virtual disk will use the entire 90GB of space) and a network portgroup able to reach the vCenter Server.
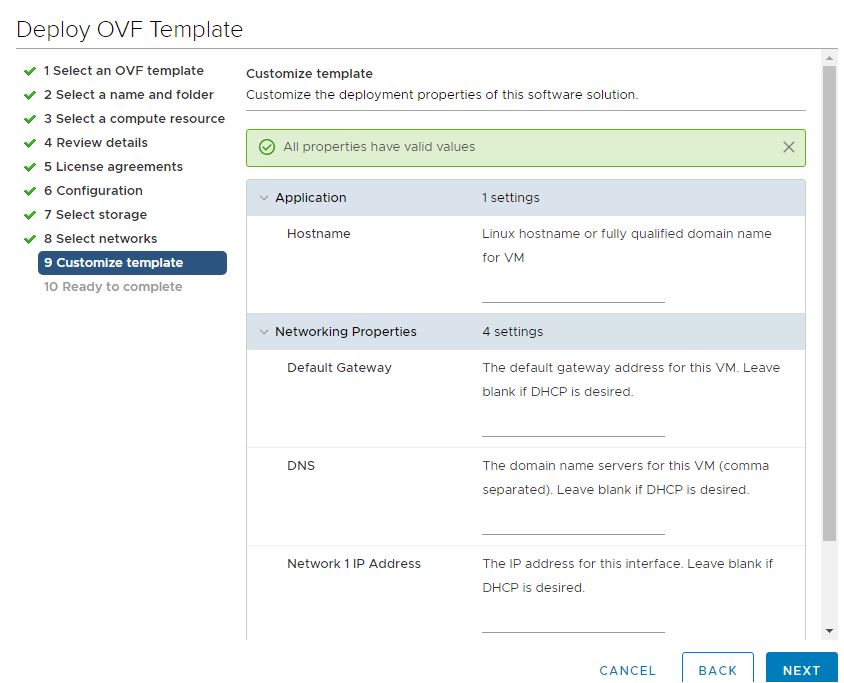
At this point you have to pass all the parameters needed for the guest customization, but if you have a DHCP server you can simple leave all the fields empty!
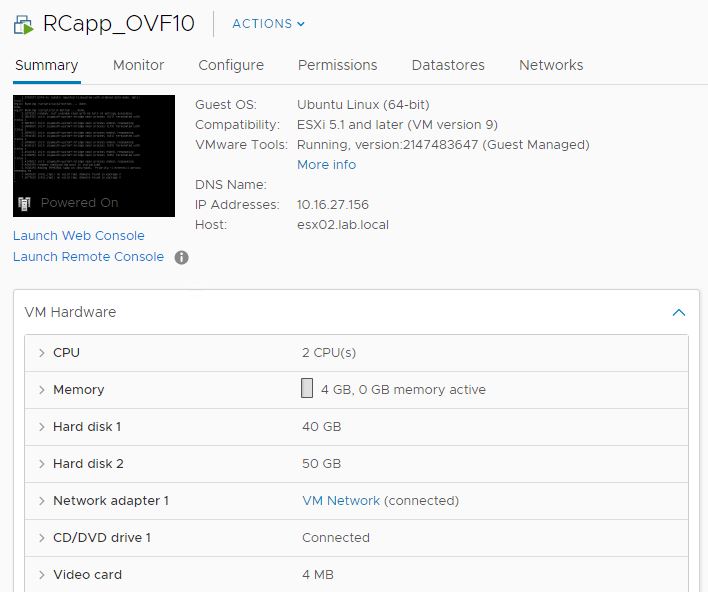
Now you can power-on the VM. Note that the VM has a guest managed VMware Tools useful to get your IP address, in case you are using a DHCP auto-configuration:
At this point, you can use your browser and just open this page: https://Runecast_VA_IP
Default credential are documented in the user manual:
- user: rcuser
- password: Runecast!
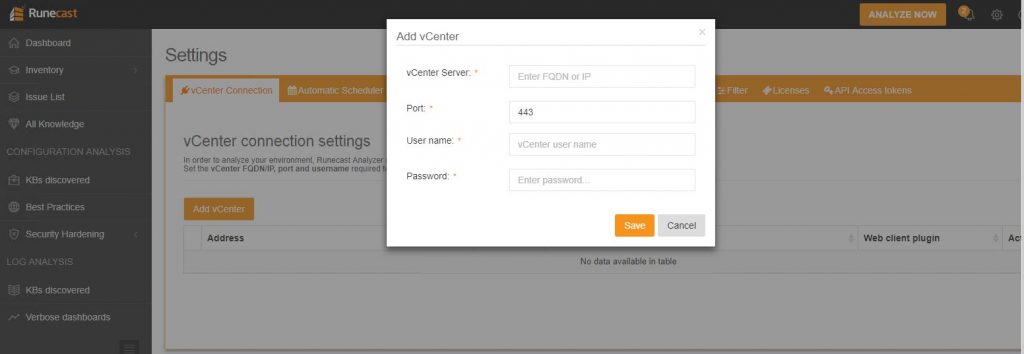
Now the first step it’s just add your vCenter Server (via IP or name):
Note that are supported also all version 5.x of vSphere (but for Meltdown and Spectre make sense analyze only 5.5 versions of later). For the vSphere Web Client integration version 6.x of vSphere is needed, but you can complete the analysis also without this integration.
Now just start a scan of your infrastructure… it’s quite fast and in few minutes will be completed:
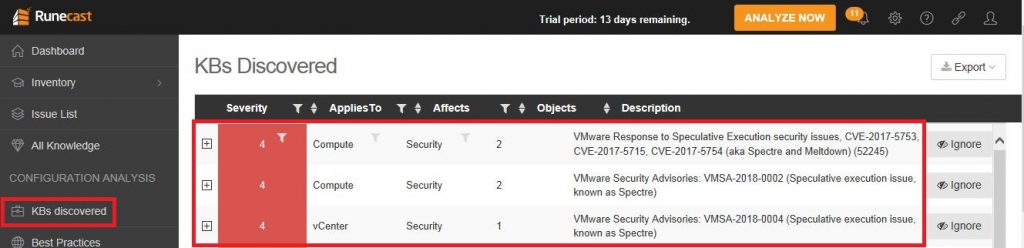
Now you can check the report in the KBs discovered section, in case of affected system you will have some report like this:
In less than 15 minutes you can deploy the VA, configure it and run the healt check. Very fast and effective.
In the report are provided also the references and some information for fix the result, but no automation to apply the required patches.
And note that does not check your hardware BIOS and firmware or your guest VM information. This detection it’s limited to ESXi and vCenter versions.