This year has started with the revelation of the Meltdown and Spectre vulnerabilities afftecting most of the (old and new) processors including Intel, AMD and ARM… but also others.
In little less than one year we are still far from the solution because there are some patches, but those patches have serious performance impacts and sometimes are those patches require more and more time to become effective (instead of causing new issues).
Neither the promise that new the new Intel’s new 9th Gen CPUs will solve those problem is necessary a good point.
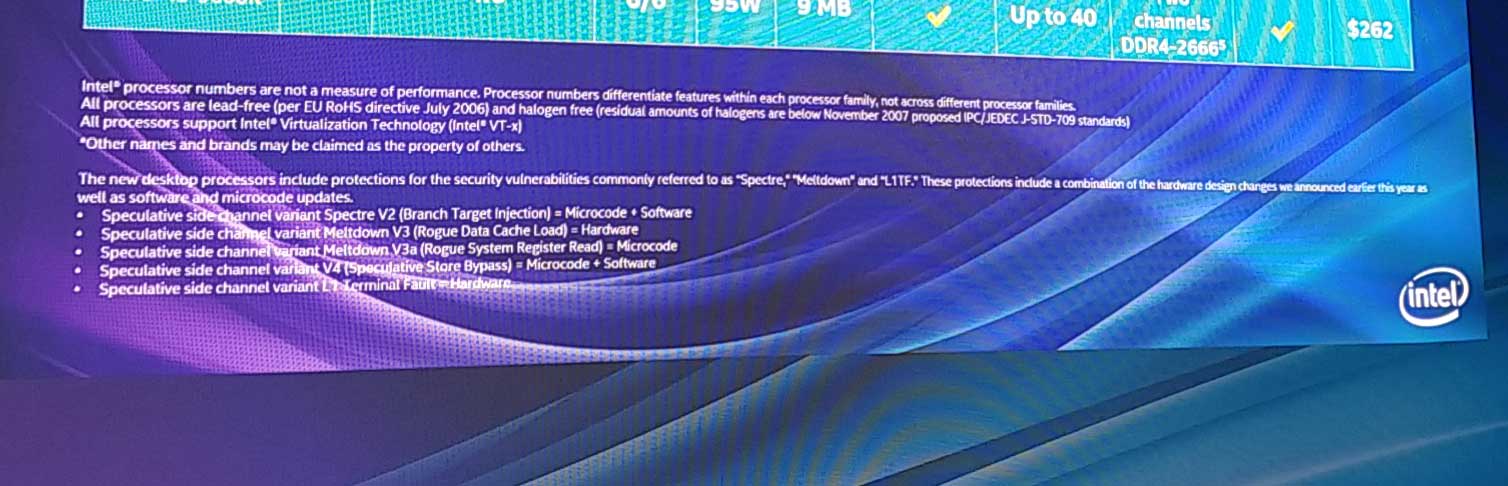
First because the solution still is not totally hardware assisted. The new desktop processors include protections for the security vulnerabilities commonly referred to as “Spectre“, “Meltdown” and “L1TF“. These protections include a combination of the hardware design changes we announced earlier this year as well as software and microcode updates.
- Speculative side channel variant Spectre V2 (Branch Target Injection) = Microcode + Software
- Speculative side channel variant Meltdown V3 (Rogue Data Cache Load) = Hardware
- Speculative side channel variant Meltdown V3a (Rogue System Register Read) = Microcode
- Speculative side channel variant V4 (Speculative Store Bypass) = Microcode + Software
- Speculative side channel variant L1 Terminal Fault = Hardware
Anyway this will be the new K-series of gaming CPUs that is the only (yet) to receiving the fix. Those chips come with changes at the hardware level and should be far more secure against the kind of attacks that Spectre and its ilk have brought to light in recent years.
Xeon CPU are still based on Skylake-X architecture and it will require more time to re-architecture the processors (this will require more years considering the design timing of a modern CPU).
And anyway, the research continue and actually seven newly attacks have beend discovered with new two variants of Meltdown (Meltdown-PK and Meltdown-BR) and new five variants of Spectre:
- Meltdown-PK (Protection Key Bypass)—On Intel CPUs, an attacker with code execution ability in the containing process can bypass both read and write isolation guarantees enforced through memory-protection keys for userspace.
- Meltdown-BR (Bounds Check Bypass)—Intel and AMD x86 processors that ship with Memory Protection eXtensions (MPX) or IA32 bound for efficient array bounds checking can be bypassed to encode out-of-bounds secrets that are never architecturally visible.
- Spectre-PHT-CA-OP (Cross-Address-space Out of Place)—Performing previously disclosed Spectre-PHT attacks within an attacker-controlled address space at a congruent address to the victim branch.
- Spectre-PHT-SA-IP (Same Address-space In Place)—Performing Spectre-PHT attacks within the same address space and the same branch location that is later on exploited.
- Spectre-PHT-SA-OP (Same Address-space Out of Place)—Performing Spectre-PHT attacks within the same address space with a different branch.
- Spectre-BTB-SA-IP (Same Address-space In Place)—Performing Spectre-BTB attacks within the same address space and the same branch location that is later on exploited.
- Spectre-BTB-SA-OP (Same Address-space Out of Place)—Performing Spectre-BTB attacks within the same address space with a different branch.
Are just theoretical issues or they can be used by potential attacks. Seems that some of them have already proofs-of-concept attacks on Intel Skylake i5-6200U and a Haswell i7-4790, AMD Ryzen 1950X and a Ryzen Threadripper 1920X and ARM NVIDIA Jetson TX1.
So be prepared to patch (again) your systems soon…
See also: