There is a big issue in vCenter Server, with sensitive information disclosure vulnerability in the VMware Directory Service (vmdir).
Under certain conditions vmdir that ships with VMware vCenter Server, as part of an embedded or external Platform Services Controller (PSC), does not correctly implement access controls.
A malicious actor with network access to port 389 on an affected vmdir deployment1 may be able to extract highly sensitive information such as administrative account credentials which could be used to compromise vCenter Server or other services which are dependent upon vmdir for authentication.
VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 10.0 with a huge risk if no action will be taken.
Anton Gostev from Veeam has notify this problem in his mailing list already this morning, but in this days you will get a notification from several way.
First is the embedded vCenter Server Health Check feature:
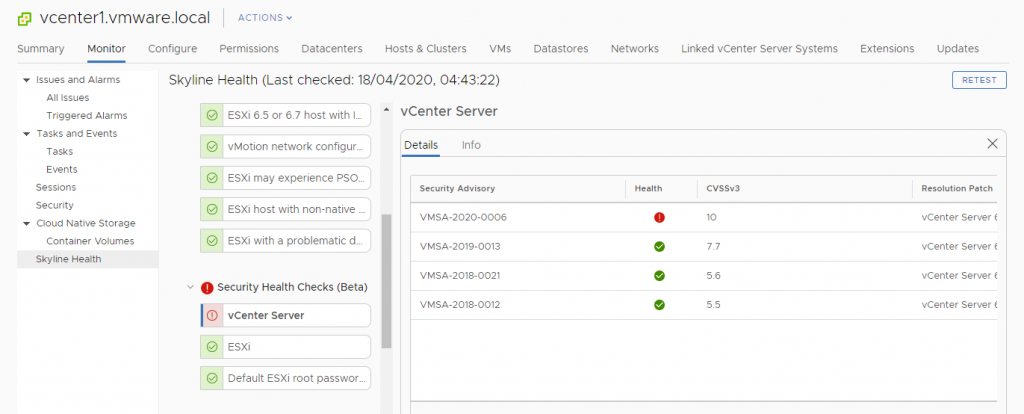
As you can notice it reports the CVE-2020-3952 issue.
Another way is using VMware Skyline:
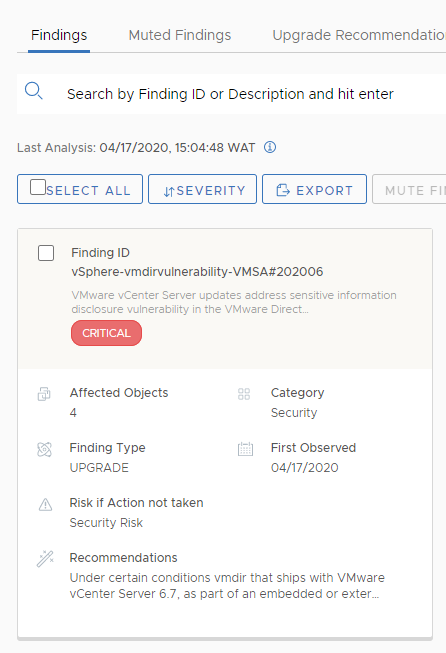
A new finding will appear.
This vulnerability affect only VMware vSphere 6.7 environments, and it is resolved in vCenter Server 6.7u3f and 7.0, so a simple update (or upgrade) fix this issue.
Note that both VCSA and vCenter Server on Windows are affected, with embedded or external PSC, but in version 6.7 only and if it was upgraded from a previous release line such as 6.0 or 6.5. Clean installations of vCenter Server 6.7 (embedded or external PSC) are not affected.
Anyway both Skyline and vCenter Health Check will detect if your system is affected.
Helpful links:











