Evolution of the security landscape
The digital security landscape has changed faster in the last years and more in the last months with the COVID-19 pandemic.
People are working more and more from home with smart working, but not all companies are prepared to secure those access and their digital workspace.
The consequence is that there are more attack and threads the are focused on people instead of corporate services or infrastructures.
But also, the rising of the cloud services model makes the attack easier and more effective… You can buy them as a service… you can buy compromised data when you need it… and this in the parallel world of the dark web.
New approaches are needed
The new type of threads requires a new type of approach and security products.
Defense in depth could be a good starting point but is not more enough and security is not only a collection of multiple layers of products and solutions.
You need integrated solutions that can also adapt faster as possible and automate much more process as possible, for example with the DevSecOps framework.
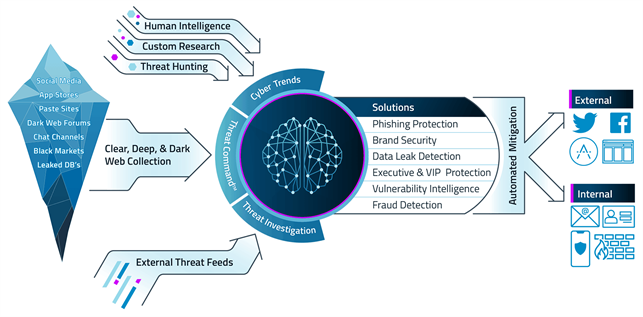
And include the continuous monitoring of an enterprise’s external digital profile across the clear, deep, and dark web to identify emerging threats and orchestrate a proactive response.
Also, compliance regulations, including GDPR, PCI, SOX, CCPA, HIPAA, and MAS, mandate organizations to implement policies and procedures to alert security teams and management to audit compromised data and Indicator of Compromises (IOCs) and ensure that business and customer data is protected.
Again, automation saves time and can further bolster both security and compliance posture.
IntSights
IntSights is a security company founded in 2015 by former members of an elite intelligence unit in the Israel Defense Forces.
Today, IntSights is trusted by many of the world’s largest companies to detect, analyze, and neutralize cyber threats across the clear, deep, and dark web. Equipped with a deep understanding of how threat actors think, collaborate, and act, they set out to build a solution that enables companies to use external intelligence to change the way they protect themselves.
They have different products and can address new security issues:
- Threat Command – https://intsights.com/products/threat-command
- Threat Intelligence Platform (TIP) – https://intsights.com/products/threat-intelligence-platform
- Vulnerability Risk Analyzer – https://intsights.com/products/vulnerability-risk-analyzer
- Threat Third Party – https://intsights.com/products/threat-third-party
And also some services:
- IntSights Services
- Security Advisory Services
- Compliance Assessment and Advisory Services
Together make it possible turn external intelligence into effective security actions:
Let’s see more details on one product: TIP
Threat Intelligence Platform (TIP)
The IntSights TIP delivers the vital functionality that operationalizes the extensive threat intelligence delivered by Threat Command, providing a comprehensive solution to address new modern threads.
The extensible IntSights TIP operationalizes threat intelligence by uniting all the tools in your security infrastructure making it possible accelerate the transition to a DevSecOps model with streamlined threat operations.
Of course, power without control is not effective and TIP automates aggregation and organization of all threat data sources into one easy-to-use dashboard. Using single-pane-of-glass visibility and real-time context can enable intuitive ranking of investigation efforts make more effective the security solution.
But not only… automation is not limited to detection; it can be also extended to the remediation processes. The raw indicators can become actionable, enriched intelligence operations or integrated with existing solutions to scale your efforts by leveraging internal security policies, practices, and tools to deliver immediate context and value.
And security attacks or threads are usually part of a more complex security violation pattern. The ability to correlate new IOCs with your unique digital assets helps to better understand the potential impact, your security risks and also prevent some attack chains or escalations.












