Some weeks ago I learn a new curios thing in a thread in the VMware Community: also the latest version of ESXi still have a VNC Server for the VM console that can be used with a common VNC connection as described in the old KB1246 (Using a VNC Client to Connect to Virtual Machines) related to the VMware GSX Server product!
Note: as written in the KB VMware does not support running virtual machines with a VNC client. The right client to access the VM console is still the vSphere Client (or the Web Client), and of course, protocols implemented in the guest OS.
This function is configured at VM but is provided at host level, so you must use different VNC ports for each VM that you want to manage with VNC.
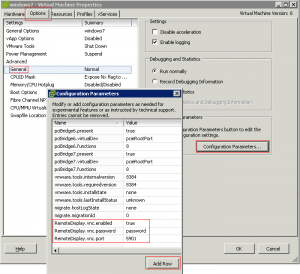
To configure each VM edit the VMX file or use the vSphere Client to edit the Virtual Machine Properties to add the following lines:
- RemoteDisplay.vnc.enabled = TRUE
Setting this option to TRUE enables standard VNC support. This setting is valid only while the virtual machine is running. If the virtual machine is powered off, you cannot connect to it with a VNC client. - RemoteDisplay.vnc.port = TCP_Port
Specify the port the VNC client uses to connect to the virtual machine (5900 is the default VNC port). If you want to connect to more than one virtual machine on the same host with a VNC client, you must specify a unique port number for each virtual machine. VMware suggests you use a port number in the range from 5900 to 5999. You can use any port number, but keep in mind that certain port numbers are used by other applications while others are privileged (meaning only the root or Administrator user can listen). For example, the VMware Management Interface uses ports 8333 and 8222; on Linux, only root can listen to ports up to port number 1024. Conflicts can occur if you specify a port in use by another application. - RemoteDisplay.vnc.password = password
Support for the VNC 3.3 authentication, which is an eight character password. Use this password when you are prompted for authentication as you use the VNC client to connect to the virtual machine.
In this example, the TCP 5901 port is used and the password is set to “password” (without the quotes):
 Now, on ESXi 5, you must add a new custom firewall rule, as described in William Lam post (How to Create Custom Firewall Rules in ESXi 5.0).
Now, on ESXi 5, you must add a new custom firewall rule, as described in William Lam post (How to Create Custom Firewall Rules in ESXi 5.0).
First step is build a new rule like this:
~ # cat /etc/vmware/firewall/vnc.xml
VNC
inbound
tcp
dst
5901
outbound
tcp
dst
0
65535
true
false
Then you can refresh the firewall rules and check that the new one is correctly loaded:
~ # esxcli network firewall refresh ~ # esxcli network firewall ruleset list | grep VNC VNC true
Finally you can simple download a VNC client (like the TightVNC Viewer) and simple connect at the IP of the ESXi host at port 5901 (using the IP:5901 syntax).