As described in the release notes, one of the new features of View5 is the certificate check from the View Client (similar as the certificate check of the vSphere Client):
Updated client certificate checking for View clients – View clients now follow the well-known browser model for handling certificates, displaying errors detected in the certificate presented by View Connection Server, or in the certificate trust chain. Administrators can set the Certificate verification mode group policy to enforce strict certificate checking; if any certificate error occurs, the user cannot connect to View Connection Server. Alternatively, administrators can use the default Warn But Allow mode, which supports self-signed server certificates and lets users connect to View Connection Server with certificates that have expired or are not yet valid. If necessary, administrators can also set a No Security mode that lets users connect without certificate checking.
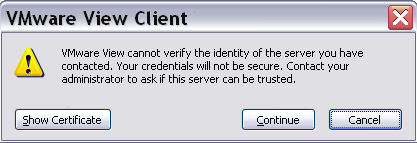
This feature is important for security reasons, but after a View 5 upgrade, can create some “diseases” for the users with the standard self-signed certificates. Each time that a user open the View Client a warning message is prompted (without any way to disable or permanent ignore it):
There are two different type of solution:
- Replace the self-signed certificates with other that are signed by an official public CA (or at least by the internal CA).
- Disable this check.
The recommend solution is replace the certificates and there are several site with the righ steps (for example see on VMware Community or on SSL certificates in VMware View environments).
But for small and simple environment, maybe could be simple disable the check. For this purpose a specific GPO rules must be enabled, as described in VMWare View 5.0 Client – Remove Certificate Warning Message at Startup.
But what’s happen for the clients that are not in the AD domain? The GPO must be applied on the side of the View Client, so a simple solution is apply the result of the GPO, by manually change the Windows Registry entries. In this case is quite simple because only a key is required (note that the Security branch may not exist in your Registry):
[HKEY_CURRENT_USERSoftwareVMware, Inc.VMware VDMClientSecurity]
“CertCheckMode”=”0”