This post is also available in: Italian
Reading Time: 3 minutesVMware has released (on Feb, 15th) a new vCSA version: vCenter Server 6.5 U1f, with build number 7801515.
This release patches the vCSA operating system (Photon OS) mainly against two vulnerabilities: bounds-check bypass (Spectre-1, CVE-2017-5753) and rogue data cache load issues (Meltdown, CVE-2017-5754). As of now, there is still no patch for branch target injection vulnerability (Spectre-2, CVE-2017-5715).
VMware has also updated the security advisory dealing with all of its virtual appliances updates for Spectre and Meltdown vulnerabilities, VMSA-2018-0007. But note that VMSA-2018-0004.2 has not been updated yet, and it still report that the suggested version for vCenter 6.5 is still 6.5U1e!
It’s funny that the Linux kernel has already been patches (for most of the issues) several weeks ago, in this case having a customized Linux version and using a virtual applicance could be a cons (but this is a most general discussion about pro and cons of VA).
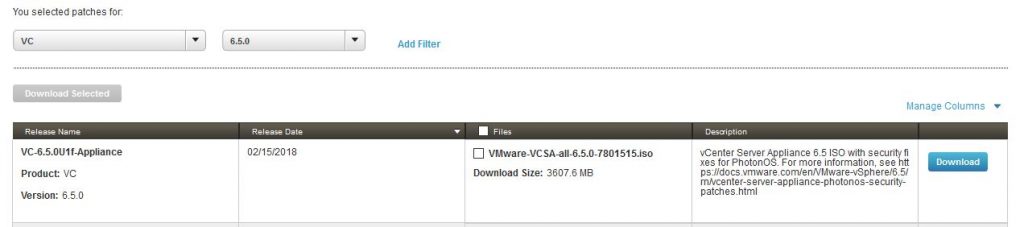
At thist point the patch is still available only on the patch repository and not on the official download page of vSphere 6.5 where the lastest version remain 6.5U1e. For the same reason the release notes are still missing.
For how install this patch, you can follow this good post, but the beauty of the vCSA is that you can manage the entire update process using the VAMI interface.
But note that after the update, you have to follow also the KB 52312: vCenter Server Appliance (and PSC) 6.5 / 6.0 Workaround for CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 (aka Spectre and Meltdown).
The vCenter Server Appliance team has investigated CVE-2017-5753, CVE-2017-5715, and CVE-2017-5754 and determined that the known attack vectors for this vulnerability can be removed by performing the steps detailed in either workaround in this article. This workaround is meant to be a temporary solution only and permanent fixes will be released as soon as they are available.
All users with roles of “Operator” may not be able to perform actions that were previously possible while the workaround is in place. This is the only functionality impact known at the time of publishing this article.
One possible workaround is to remove the access to the appliance shell for non-root users:
- Login to the vCenter Server Appliance with an SSH session and the root user.
- Backup the /etc/passwd file by with this command:
- To list all users, run this command in the appliance shell and take note of the users listed:
- Open the /etc/passwd file with a plain text editor using this command:
- Search for all non-root users who have operator access.
- Change the default shell access from /bin/appliancesh to /sbin/nologin.
- Save and exit the file
To confirm that the workaround run these steps:
- Attempt to log into vCenter Server Appliance using SSH and user with the Operator role.
- Operator users should no longer be able to log in.