VMware la rilasciato (ancora il 15 febbraio) una nuova versione della vCSA version: vCenter Server 6.5 U1f, che porta il build number a 7801515.
In questa nuova versione della vCSA viene aggiornato il Photon contro due delle vulnerabilità relative alle problematiche Meltdown e Spectre.
La nuova patch vCenter Server 6.5 U1f risolve le problematiche bounds-check bypass(Spectre-1, CVE-2017-5753) e rogue data cache load (Meltdown, CVE-2017-5754). Per la vulnerabilità branch target injection (Spectre-2, CVE-2017-5715) non c’è invece ancora nessuna patch.
VMware ha aggiornato il documento VMSA-2018-0007, ma non ancora il VMSA-2018-0004.2 che riporta come ultima versione del vCenter il 6.5 is still 6.5U1e! Notare che la patch non è elencata nel download del vCenter, ma solo nella pagina delle patch repository: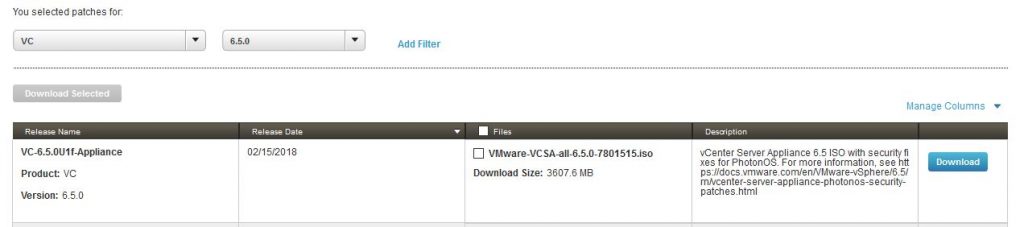
E’ possibile comunque utilizzare VAMI aggiornare in modo semplice e veloce il vCenter.
I package aggiornati sono i seguenti:
- linux 4.4.110-2
- libgcrypt 1.7.6-3
- c-ares 1.12.0-2
- ncurses 6.0-8
- libtasn1 4.12-1
- wget 1.18-3
- procmail 3.22-4
- rsync 3.1.2-4
- apr 1.5.2-7
Notare però che alla fine bisogna seguire anche la KB 52312: vCenter Server Appliance (and PSC) 6.5 / 6.0 Workaround for CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 (aka Spectre and Meltdown).
The vCenter Server Appliance team has investigated CVE-2017-5753, CVE-2017-5715, and CVE-2017-5754 and determined that the known attack vectors for this vulnerability can be removed by performing the steps detailed in either workaround in this article. This workaround is meant to be a temporary solution only and permanent fixes will be released as soon as they are available. All users with roles of “Operator” may not be able to perform actions that were previously possible while the workaround is in place. This is the only functionality impact known at the time of publishing this article. One possible workaround is to remove the access to the appliance shell for non-root users:
- Login to the vCenter Server Appliance with an SSH session and the root user.
- Backup the /etc/passwd file by with this command:
- To list all users, run this command in the appliance shell and take note of the users listed:
- Open the /etc/passwd file with a plain text editor using this command:
- Search for all non-root users who have operator access.
- Change the default shell access from /bin/appliancesh to /sbin/nologin.
- Save and exit the file
To confirm that the workaround run these steps:
- Attempt to log into vCenter Server Appliance using SSH and user with the Operator role.
- Operator users should no longer be able to log in.













