Linux Kernel 4.15 has been released on 28 Jan 2018 and, thanks to the entire Linux Kernel development team, this release contains the latest code to deal with Meltdown and Spectre issues and minize the related risks.
The Kernel is the core code in the operating system managing low level tasks. In the update both vulnerabilities are explicitly addressed.And the interesting aspect is that the performance are not so bad!
There are infact three instinct vulnerabilities identified, one Meltdown and two variations of Spectre (known as v1 and v2). Kernel 4.15 actually address only Meltdown and Spectre v2 issues.
For Meltdown avoidance (needed for Intel CPUs only) there is a feature called Page Table Isolation (PTI) that prevents exploiting Speculative Execution. Users can choose to turn it off with a the special pti=off kernel boot option.
For Spectre v2 the fix (available for both Intel and AMD processors, not yet for ARM), the fix comes in the form of a retpoline mechanism. It requires use of a compiler (GCC) that is compatible, so users will need to update accomplying fixes as well. The Spectre-inhibiting mechanism can be turned of. To do so, use the spectre_v2=off option at boot time.
So the Spectre v1 vulnerability is still at large, but difficult to exploit. The Linux Kernel Runtime Guard (LKRG) seems that can address the kernel security in other ways, but is still too primordial to be used in an effective way.
The interesting aspect is that the performance are not so bad: Linux user benchmarking recent kernel versions on a specific network-heavy load and it’s really promising, with “4.15 is 7-9% faster than 4.11”.
But of course without the security patches: “Turning kpti on makes 4.15 1-2% slower than 4.11”. So with the security patches the system is little slowest than before. Not so bad, considering that the (initial) expect overhead where around 20-30%!
So, overall, we are right back where we started from. Which makes me feel good, the recent Meltdown changes turn out to not really be much of a problem overall.
But if you are stuck at an old kernel version (i.e. 3.10.y, 4.4.y, or 4.9.y or whatever your distro is camping on for the next decade), that’s a totally different story. Go forth and benchmark! Then go update to a newer kernel version, odds are it will be a good improvement.
So, how and you update your kernel on your distribution that still does not include it, and usually apply backported patches to old kernels?
There is a great blog post with several hints for the major distributions.
For CentOS (or RHEL) 6 or 7 you can use an external repository: ELRepo and install the latest Kernel from there.
First import the ELRepo repository key.
# rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
Next, add ELRepo:
On CentOS 7 / RHEL 7 / Scientific Linux 7:
# rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-3.el7.elrepo.noarch.rpm
On CentOS 6 / RHEL 6 / Scientific Linux 6:
# rpm -Uvh http://www.elrepo.org/elrepo-release-6-8.el6.elrepo.noarch.rpm
Enable ELRepo fastest mirror:
# yum install yum-plugin-fastestmirror
Finally, install the latest Linux kernel 4.15 version using command:
# yum --enablerepo=elrepo-kernel install kernel-ml
Check your grub configuration to enable the right kernel (the 4.15 kernel) during the boot, then reboot your system.
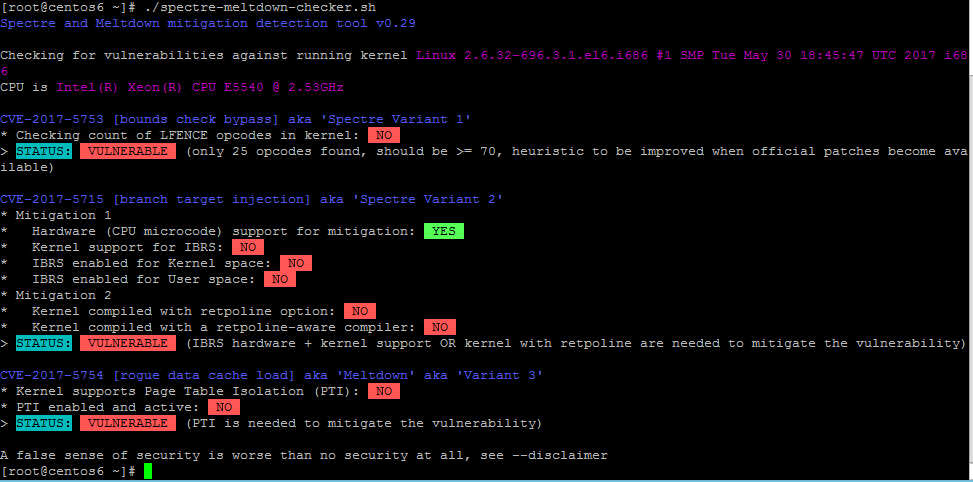
To check the status for the Meltdown and Spectre protection, you can use the powerful shell script spectre-meltdown-checker available on GitHub. You can download it with this command:
wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
And then just run it to check your status. For example for a not patched kernel:
The kernel 4.15 it’s not limited only to Meltdown and Spectre patches, but there were also a few more things worth pointing out:
- AMD got support for Secure Encrypted Virtualization. This allows the kernel to fence off the memory a virtual machine is using by encrypting it. The encrypted memory can only be decrypted by the virtual machine that is using it. Not even the hypervisor can see inside it. This means that data being worked on by VMs in the cloud, for example, is safe from being spied on by any other process outside the VM.
- AMD GPUs get a substantial boost thanks to the inclusion of display code. This gives mainline support to Radeon RX Vega and Raven Ridge cards and also implements HDMI/DP audio for AMD cards.
- Raspberry Pi aficionados will be glad to know that the 7” touchscreen is now natively supported, which is guaranteed to lead to hundreds of fun projects.