The new build of Windows 10 have a lot of new security settings and some of them can make cause issues with VMware Workstation (or potentially also other host hypervisors).
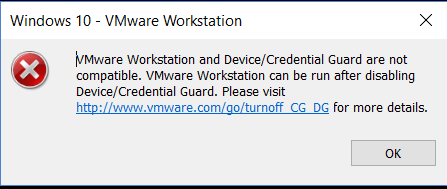
One common issue when you try to power on a VM in Workstation and instead you get this error message:
VMware Workstation and Device/Credential Guard are not compatible. VMware Workstation can be run after disabling Device/Credential Guard.
The VMware KB 2146361 (Powering on a vm in VMware Workstation on Windows 10 host where Credential Guard/Device Guard is enabled fails with BSOD) describe this issue. But it’s not complete.
According to with this KB, powering on a VM in VMware Workstation prior to version 12.5 on a Windows 10 host where Credential Guard or Device Guard is enabled fails with a blue diagnostic screen (BSOD). Device Guard or Credential Guard are incompatible with Workstation, just because use Hyper-V feature to provide a better isolation.
To disable Device Guard or Credential Guard the first step is the following:
- Disable the group policy setting that was used to enable Credential Guard.
- On the host operating system, click Start > Run, type gpedit.msc, and click Ok. The Local group Policy Editor opens.
- Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Device Guard > Turn on Virtualization Based Security.
- Select Disabled.
There are also other setting described in the KB, but the point is that you can get this error message also for other reason, not related to Device Guard or Credential Guard or Hyper-V.
In the following build, new security features have been added:
- Windows 10 Enterprise edition, version 1709 or higher
- Windows 10 Professional edition, version 1803
One is Application Guard. Designed for Windows 10 and Microsoft Edge, Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted web sites, cloud resources, and internal networks. Everything not on your list is considered untrusted.
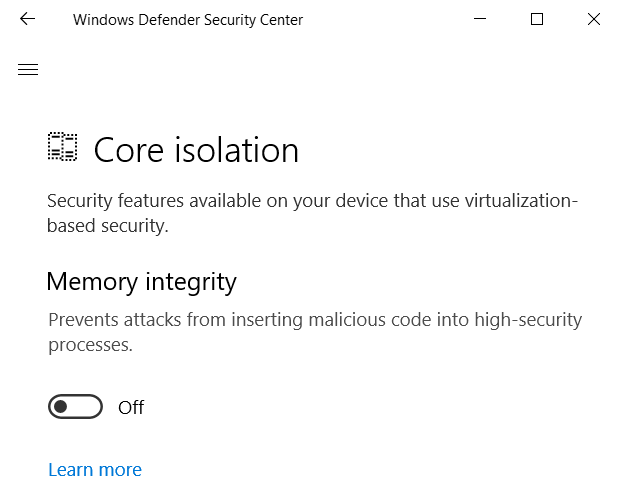
But there is the Windows 10 Core Isolation that can cause this issue. This feature has two different security components:
- Core isolation: Core isolation provides added protection against malware and other attacks by isolating computer processes from your operating system and device.
- Memory integrity: Memory integrity is a feature of core isolation.
By turning the Memory integrity setting to On, you can help prevent malicious code from accessing high-security processes in the event of an attack. For more information see this blog post.
You must be signed in as an administrator to turn on or off Memory integrity. But the funny part is that after you enable it (and after the reboot) you cannot disable in a simple way (the setting become manageable only with group policies).
One simple way to disable is to change this registry key and set the value to 0.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity
Then you need to reboot you system and Workstation will be able again to power-on the VMs.