Minimum viability refers to the set of essential resources and capabilities (combination of critical applications, assets, processes, and people) an organization needs to maintain critical operations and fulfill its core mission after a disruption like a cyberattack or disaster.
It’s about identifying what’s absolutely necessary to get back up and running quickly and efficiently, rather than trying to restore everything at once.
The rise of cyberattacks is forcing organizations to rethink their recovery strategies. While detecting threats remains critical, a more significant challenge has emerged: making sure protected data is clean and available to bring a company back online.
Why minimum viability is so important?
- For rapid recovery: Minimizing the time it takes to restore essential operations is crucial for minimizing financial losses and maintaining customer confidence.
- To maintaining mission: Ensuring that core operations can continue, even after a significant disruption, is vital for an organization’s long-term viability.
In order to develop a proper plan for minimum viability you need:
- Accurate and aligned view of the core processes and dependent systems.
- Understanding the cost of downtime for those core resources.
- Clear and actionable plan to restore critical systems, data, and processes.
How do you achieve minimum viability in practice?
First step is identify your critical assets:
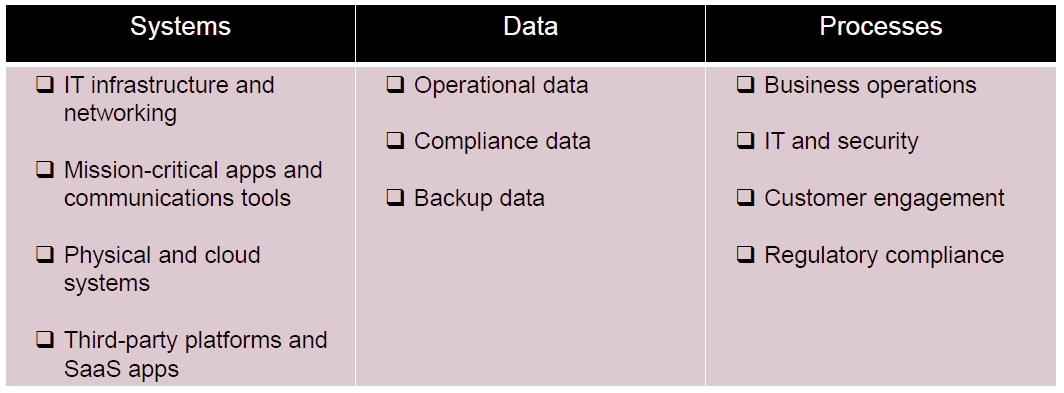
Second step is to assess the impact: every minute of downtime costs you… but how much? Do you understand the effects of downtime on each of your critical assets? Revenue loss. Regulatory fines. Brand and reputation damage. Understanding the cost is vital to decision-making and helping prioritize your recovery.
Then you need to build your plan and also test it.
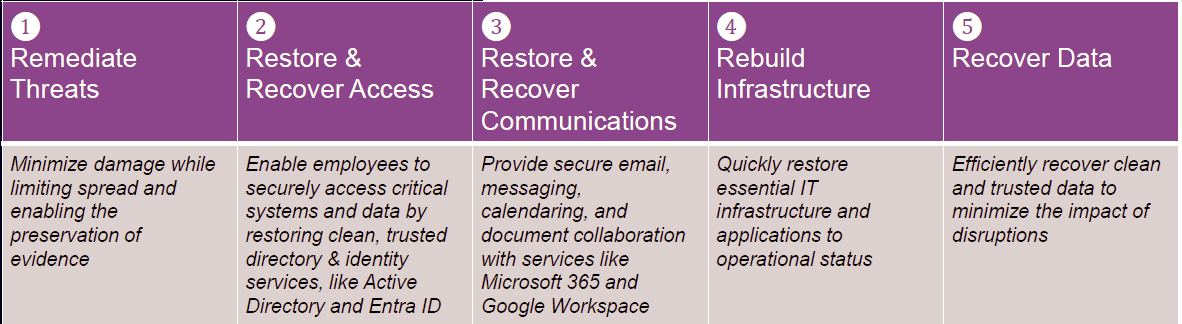
There are also some nest practices for achieving minimum viability:
- Air-gapped copies of data: Keep immutable, indelible copies of critical data in at least one airgapped cloud environment.
- The ability to identify last-known-good: Establish and test practices, processes, and automation to verify clean recovery points for critical applications, infrastructure, data that are part of your minimum viability.
- Frequent testing of plans: Run simulations and actual recovery exercises to build confidence that you can restore and operate the applications, infrastructure, and data that you need for minimum viability.
- Use an isolated recovery environment (IRE): Since you can’t trust your data or infrastructure, an IRE remains safe from these attacks and allows you to restore systems and data securely, in a known-clean environment.
- Isolate infected/compromised data for forensics: By isolating your infected and compromised systems, your security teams can do in-depth analysis without the risk of reinfection or lateral movement.
For more information see also the Commvault’s guide to minimum viability.